How to setup site2site OpenVPN connection using Asus RT-AC66U_B1 routers running Asuswrt-Merlin firmware
The OpenVPN is an open multiplatform VPN solution, which allowing variety of configuration. The standard use-case is client2network setup, allowing the remote client to “dial-in” into network. Other scenario is site2site configuration, allowing seamless communication of each network device across both sites.
Description of my environment
I have two Asus RT-AC66U_B1 running Asuswrt-Merlin firmware version 384.9 with following network configuration:
- Client side:
- Router IP: 192.168.33.1
- Netmask: 255.255.255.0
- Server side:
- Router IP: 192.168.22.1
- Netmask: 255.255.255.0
Prerequisites
- DDNS has to be active on server side the (I use the standard *.asuscomm.com DDNS service)
- DDNS on client side is optional, but I recommend it for remote access via Asus AiCloud app
- JFFS filesystem enabled and formatted
Setup site2site
The setup consists of two steps:
- Setup standard client2network connection
- Modify the connection to site2site setup
Setup standard client2network connection
Configure server side router
- Log on to the server side router (192.168.22.1)
- Select VPN from the left-hand menu and click on VPN Server tab and click on OpenVPN switch

You can setup two VPN server configuration. We will now setup the Server 1 configuration
- Flip Enable OpenVPN Server switch to ON position (will change to green)
You are now in General settings section.

- Tick the LAN only radio button
- Add some user/password in the table below by entering username and password into text fields and click on the plus button

- Then hit Apply, this will take some time
- Select Advanced Settings option in VPN Details dropdown box

- Set following parameters to:
- Interface Type: TUN (routed networks)
- Protocol: TCP (do not try UDP, will not work afterwards wit site2site modifications!)
- Username/Password Authentication: Yes (for now, we will use simple authentication, reconfiguration for use of cert logins will be discussed in another article)
- VPN Subnet/Netmask: is irrelevant, leave the default one
- Advertise DNS to clients: No
- Compression: Disable (enabling has for sure impact to router utilization and transfer speed – not tested yet)
- At Manage Client-Specific Options select Yes – you will get additional input fields
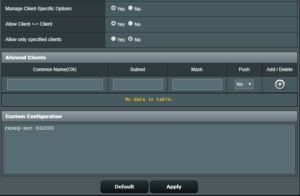
- Select Yes at the Allow Client <-> Client option
- In the Custom Configuration enter following recommended parameter
reneg-sec 432000
- Hit the Apply button – will take some time.
If everything is fine (no fatalities), you should get the General VPN Details page and the Enable OpenVPN Server should be in ON position and green.
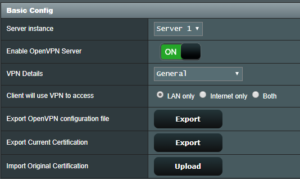
- Now, you have some new buttons available, hit the first Export button (Export OpenVPN configuration file) – one file named “client1.ovpn” will be downloaded
- Open the file as text file and check the first lines: for tun, tcp-client options and the correct DDNS name of the server-side router
client
dev tun
proto tcp-client
remote myprimarysite.asuscomm.com 1194
Configure client side router
- Log on to the client-side router (192.168.33.1)
- Select VPN from the left-hand menu and click on VPN Client tab and click on OpenVPN switch
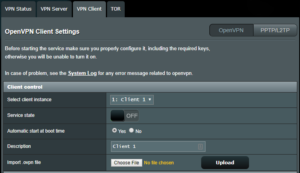
- Click on Choose File button on Import .ovpn file option, select the previously downloaded “client1.ovpn” file and hit Upload.
- Set Automatic start at boot time to Yes
- Check the lines Interface Type, Protocol and Sever Address for correct values

- Ensure the Username/Password Authentication is Yes
- Enter the username and password set on the server-side router
- Scroll down to Advanced Settings
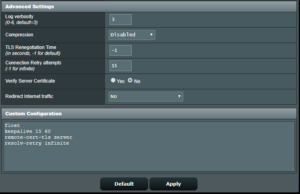
- Check that Verify Server certificate is set to No
- The directives in Custom Configuration are imported from “client1.ovpn” file – don’t touch them
- Hit Apply button – takes again some time
- Flip the Service state switch to ONIf anything is fine (no fatalities), the Service state switch should be green with yellow Connected message.
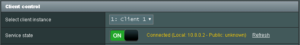
At this moment any network device should be able to ping/connect to any network device on the server-side network.
The basic setup for client2network setup or “dial-in” setup if finished, let’s go one step beyond and configure the “return direction”
Modify the connection to site2site setup
Configure server side router
- Log on to the server-side router (192.168.22.1)
- Select Administration from the left-hand menu and click on System tab
- Enable the SSH access as shown:

- Check the JFFS2 section

- If the config is like shown, no action is needed, otherwise set both parameters to Yes and reboot the server
- Use some SSH client (like puTTy – can be downloaded here: https://www.chiark.greenend.org.uk/~sgtatham/putty/) and log in into router
- Run following commands to create directory for OpenVPN client specific configuration
(please note: the “ccd1” folder is for Server1 and if you want to use Server2, you need directory “ccd2”)
root@RT-AC66U_B1-5668:/temp/home/root# cd /jffs/configs
root@RT-AC66U_B1-5668:/jffs/configs#
root@RT-AC66U_B1-5668:/jffs/configs# mkdir openvpn
root@RT-AC66U_B1-5668:/jffs/configs# cd openvpn
root@RT-AC66U_B1-5668:/jffs/configs/openvpn# mkdir ccd1
root@RT-AC66U_B1-5668:/jffs/configs/openvpn# cd ccd1
root@RT-AC66U_B1-5668:/jffs/configs/openvpn/ccd1#
- Using vi create file called as the entered username, in this case “Remote1”
root@RT-AC66U_B1-5668:/jffs/configs/openvpn/ccd1# vi Remote1
- And enter following line, which tells the server-side router that some network exists:
iroute 192.168.33.0 255.255.255.0
- Save the file (enter “:wq” command)
- Close puTTy and log into router’s web interface
- Select VPN from the left-hand menu and click on VPN Server tab
- Go to Advanced Settings
- Change the content of Custom Configuration to following:
reneg-sec 432000
username-as-common-name
push "route 192.168.22.0 255.255.255.0"
client-config-dir /jffs/configs/openvpn/ccd1/
route 192.168.33.0 255.255.255.0
- Hit the Apply button – will take some time
Configure client side router
- Log on to the client-side router (192.168.33.1)
- Select VPN from the left-hand menu and click on VPN Client tab
- In section Network Settings set the parameter Create NAT on tunnel to No
- *UPDATE* set the new parameter Inbound Firewall to Allow
- Hit the Apply button – will take some time
Final words
After reconnecting the tunnel the communication should be possible in both directions
Disclaimer
This how-to is based on following article: https://openvpn.net/community-resources/how-to/#scope and adopted by me for my two Asus routers running Asuswrt-Merlin firmware.
(c)2019 by zolo













